By Eric Vandenbroeck and co-workers
How Crypto-Currency Fraud Functions
Fifteen years after
Satoshi Nakamoto’s Bitcoin whitepaper, cryptocurrency has exploded from an idea
for a single digital asset to a thriving asset class whose global market cap
exceeds $1 trillion. Around the world, people of varying backgrounds have embraced
crypto, using it for everything from investing to sending remittances to
hedging against inflation. Recognizing these trends, governments worldwide are
continually passing and refining crypto regulation while traditional financial
institutions think about how to incorporate crypto into their product
offerings. But despite global adoption and increased regulation, many
misconceptions about cryptocurrency persist.
In an earlier
overview, we started with Ethereum, whereby Sam Bankman-Fried's seven counts of
conspiracy and fraud make for a good starting point.
Less than a week
after several liquidity pools on Curve Finance were exploited in a
multi-million dollar scheme, the hacker returned 4,820
alETH and 2,258 ETH to Alchemix, worth around $12.7 million. These transactions were
accompanied by an encrypted
message in which the
hacker wrote, “I saw some ridiculous views, so I want to clarify that I’m
refunding you not because you can find me, it’s because I don’t want to ruin
your project, maybe it’s a lot of money for a lot of people, but not for me,
I’m smarter than all of you. . .” NFT lending protocol JPEG also confirmed receipt of most of its stolen
funds, worth around $10 million.
On August 6, 2023,
Curve Finance announced on
Twitter that the
established deadline for the hacker to voluntarily return the remainder of the
funds had passed. Thus, the company extended its bounty offer of $1.85 million
to anyone able to uncover the hacker’s identity
Investigation reveals
more than 150 fake firms are targeting people online, breaking their hearts,
and emptying their bank accounts.
Sometimes Crypto
fraud goes like this:
A woman meets a man
online. They flirt. Then, after a few weeks, they begin imagining a future
together. Fast forward a few months, and one has had their heart broken and
been defrauded of their life savings.
It sounds like a
classic romance scam, but it isn’t. This is “pig butchering”: a brutal,
elaborate, and rapidly expanding form of organized crime, often involving
criminal syndicates, modern-day slaves, and victims worldwide.

An investigation by
the Observer and the Bureau of
Investigative Journalism has
found that global organised crime gangs are using the
UK as a virtual base for their operations – systematically exploiting lax
company registration laws to carry out fraud on an industrial scale.

One east London tower
block resident has been inundated with letters addressed to businesses and
people he has never heard of.

A scam victim who
wants to remain anonymous. Many feel ‘stupid’ to have been
duped. Photograph: Andy Hall/The Observer
Key to the success of
pig-butchering scams is convincing victims that they are using a legitimate
trading platform or virtual wallet. To do this, criminal groups set up real
companies that they can then refer to on their scam websites, creating a veneer
of legitimacy.
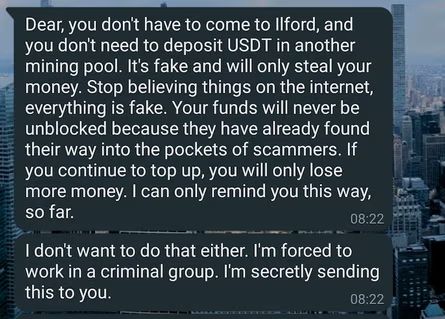
A message from a
‘scammer’ who claims they’re a victim of forced labor and being forced to carry
out this scam.
Around the world, law
enforcement agencies are working harder to tackle cryptocurrency crime. The
National Crime Agency is preparing to launch a new unit devoted
to tackling the scams. Interpol, which facilitates worldwide police
cooperation, recently set up a financial crime and anti-corruption center.
It currently costs as
little as £12 and takes a few minutes to register a company online without the
need to provide any proof of ID. The government has pledged to tighten the
rules, including introducing a requirement to verify information provided to
Companies House. However, the second part of the economic
crime bill is
yet to go before the Lords, and the timeline for its future implementation is
unclear.

Within a few years,
two brothers from Ohio were imprisoned for cryptocurrency-related crimes. The
first, Larry Dean Harmon, was arrested and
charged for a
money laundering conspiracy from his operation of Helix, a cryptocurrency
mixing service operating on the dark web. Shortly after Internal Revenue
Service Criminal Investigations (IRS-CI) seized Larry’s Bitcoin wallets, his
younger brother, Gary James Harmon, used Larry’s passwords to steal some of the
Bitcoin back from the seized wallets. In April 2023, Gary was sentenced to
four years in prison for
his theft from the government.
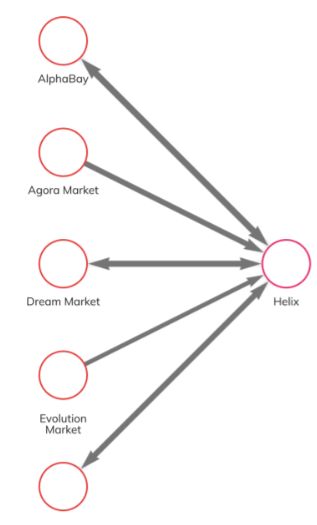
In the early stages
of the investigation, an undercover FBI
agent transferred Bitcoin from
an AlphaBay wallet to Helix and confirmed that using
the mixer reduced direct traceability to AlphaBay.
Then, law enforcement used Chainalysis to
identify 16 Bitcoin
wallets which contained
nearly 5,000 Bitcoin worth of proceeds from Helix’s operation. When law
enforcement searched Larry’s residences in Ohio and Belize, they recovered
multiple cryptocurrency storage devices linked to these wallets, and also found an
accounting spreadsheet in
his Google Drive that indicated ownership of more than $56 million worth of
Bitcoin and other assets.
After Larry’s arrest
in 2020, Gary was laid off from Coin Ninja and struggled financially. Sensing
an opportunity to acquire funds from his brother’s 16 wallets in custody, Gary
used Larry’s passwords to access several of them. He transferred 712 Bitcoin (worth more than $5 million at the time) to
eight new wallets. We can see those transactions below in Reactor.
Once complete, Gary
deposited 68 Bitcoin as collateral for a $1.2 million loan from BlockFi, which he used to purchase a luxury condo in
Cleveland, Ohio. He spent at strip clubs and on private jets. The below image
shows Gary in a
bathtub with cash at a
nightclub, which investigators recovered on his phone. Additionally, text
messages on the phone suggest he made extravagant purchases around the same
time.
On July 30, 2023,
several liquidity pools on Curve Finance were exploited, resulting in approximately $70 million in losses and
triggering panic within the DeFi ecosystem. These hacks occurred due to a
vulnerability in Vyper, a third-party Pythonic
programming language for Ethereum smart contracts used by Curve and other
decentralized protocols. Since then, several white hat hackers and MEV bot operators
have helped recover some of the funds, which means the actual value lost may
end up being lower than the total currently reported. Below, we’ll share what
we know so far about the hack.
After news broke of
the hacks, CRV declined 5%. This decline, along with the risk that malicious
hackers possessing millions’ worth of CRV could sell into the token’s
now-illiquid market, triggered fears of contagion effects
for some DeFi protocols.
In particular, AAVE's lending protocol is at risk of incurring debt due to
Egorov’s massive and well-known borrow position secured by CRV token
collateral.
At this time, Curve
has not detailed any recovery plans but publicly
advised its users to
withdraw funds from Vyper-based pools. We have
labeled all addresses relevant to the Curve hacks in Chainalysis
products and will continue to provide updates on the situation when possible.
For updates click hompage here